Code:adb shell su
+ Reply to Thread
Results 241 to 270 of 609
-
-
its look like my T95 is not root i cant becoming superuser or wont change # after type su -
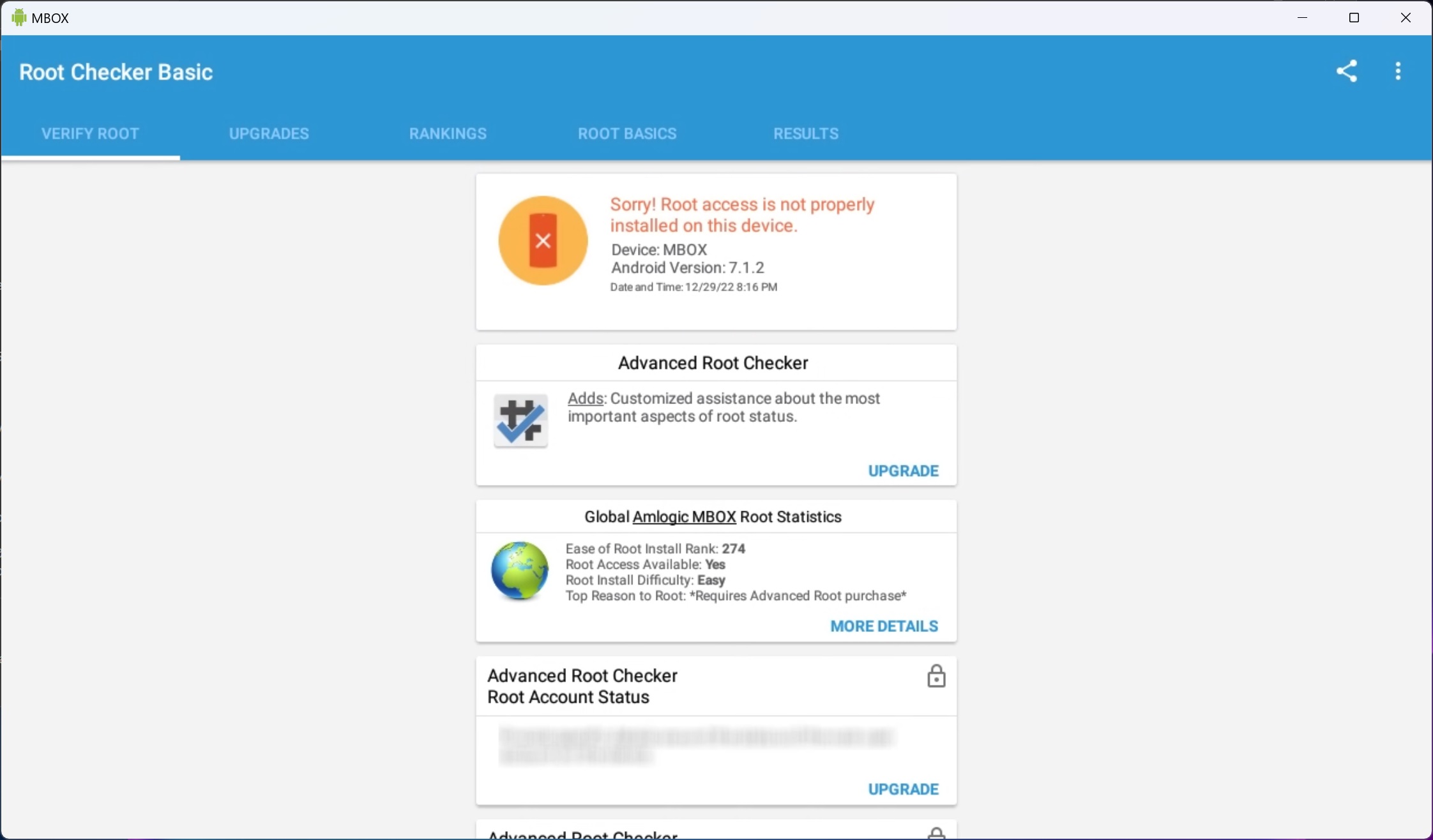
Last edited by iamghost; 29th Dec 2022 at 14:21.
-
All is not lost! Cedric has written a how-to here about getting a CDM from an Android Emulator and it will cost you nothing but an hour or so. https://forum.videohelp.com/threads/408031-Dumping-Your-own-L3-CDM-with-Android-Studio#post2676315
Last edited by A_n_g_e_l_a; 29th Dec 2022 at 14:31. Reason: punctuation!!
-
Edited first post to include an alternative to bitmovin.com for a first key-grab. Thanks to ehurdler and [ss]vegeta for reports of tg4.ie availability.
-
mybe your token "nv-authorizations" is one time use or expired fast.
or you sure u cdm is working? -
-
on header put only 'nv-authorizations': 'eyJraWQ.......
If it doesn't work, your script needs editing for your video link -
-
Hello CamelTr,
the site you are trying to get keys for is www.movistar.es.
Our sponsor, forum-head-honcho, spiritual guide and all round good bloke - HairlessRichard - will lock my thread if you continue to ask about getting keys for a subscription site. So kindly stop.
- HairlessRichard - will lock my thread if you continue to ask about getting keys for a subscription site. So kindly stop.
You may wish to try your luck in your own thread, please do, but do not pollute this one. Thank you. -
Is there a way to pass the bearer token authorization in the http request instead of in the headers.py.
-
The output of curlconverter will give a line at the bottom showing how python can construct a python POST request
If that is what you mean. And your bearer token would go as 'params' sent in the url string and not in the headers.Code:import requests headers = { 'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/110.0', 'Accept': '*/*', 'Accept-Language': 'en-GB,en;q=0.5', # 'Accept-Encoding': 'gzip, deflate, br', 'Content-Type': 'application/octet-stream', 'Referer': 'https://uktvplay.co.uk/', 'Origin': 'https://uktvplay.co.uk', 'DNT': '1', 'Sec-Fetch-Dest': 'empty', 'Sec-Fetch-Mode': 'cors', 'Sec-Fetch-Site': 'cross-site', 'Connection': 'keep-alive', # Requests doesn't support trailers # 'TE': 'trailers', } params = { 'fastly_token': 'NjQxNmRlM2NfMjYzOTgxNDA3NTVjNjI5NmMzMzhmNGU4NGZlZjhiNmE2MjI5OGQzZTU5MWQ1NmQ3NDNlMTM2NzM5ZWZlZDU5NA==', } data = 'snipped"'.encode() response = requests.post( 'https://manifest.prod.boltdns.net/license/v1/cenc/widevine/1242911124001/210fe5cf-fa90-47e4-82f6-116941637794/43835e0a-db77-4933-8daf-8e35062f20fa', params=params, headers=headers, data=data, ) -
-
I was trying my hand at the Android Studio solution and not being able to get that to work... I'm on an M1 Mac, which I think is the issue? The virtual devices don't come with Chrome installed for ARM, and installing Chrome through Terminal doesn't work-- even if that worked, it looks like apps installed that way won't interact with Widevine. The Play Store versions of the virtual devices, while capable of running Widevine correctly for installed browsers like Firefox, won't let me run frida-server.
So, I decided to re-re-retry doing this on my Samsung Tab S2 on Android 7.0. I successfully rooted the device, and when I try to boot frida-server-16.0.11-android-arm on it, it completely freezes the device until I kill the process. If I use frida-server-15.1.17-android-arm, it works, but never gets past "Hooks completed".
Like so...
Code:python3 dump_keys.py 2023-03-20 02:58:52 AM - root - 16 - INFO - Connected to SM T710 2023-03-20 02:58:52 AM - root - 17 - INFO - scanning all processes for the following libraries 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=1, name="init", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=1704, name="ueventd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2602, name="debuggerd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2603, name="mcDriverDaemon", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2604, name="vold", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2615, name="debuggerd:signaller", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2748, name="daemonsu:mount:master", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2756, name="daemonsu:master", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2781, name="healthd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2784, name="lmkd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2785, name="servicemanager", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2786, name="surfaceflinger", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2787, name="watchdogd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2788, name="cs", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2789, name="secure_storage_daemon", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2790, name="ss_conn_daemon", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2791, name="edmaudit", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2792, name="drmserver", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2794, name="apaservice", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2795, name="jackservice", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2797, name="bintvoutservice", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2798, name="argosd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2799, name="gpsd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2800, name="zygote", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2801, name="ddexe", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2802, name="connfwexe", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2804, name="sdp_cryptod", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2805, name="audioserver", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2806, name="cameraserver", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2807, name="installd", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2808, name="keystore", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2809, name="media.codec", parameters={}) 2023-03-20 02:58:52 AM - root - 19 - DEBUG - Process(pid=2810, name="mediadrmserver", parameters={}) 2023-03-20 02:58:53 AM - Helpers.Scanner - 82 - INFO - Running libmediadrm.so at 0xaa77a000 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=2811, name="media.extractor", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=2812, name="mediaserver", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=2813, name="netd", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=2815, name="at_distributor", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=2816, name="fingerprintd", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=2818, name="gatekeeperd", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3326, name="system_server", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3399, name="tlc_server", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3448, name="otp_server", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3580, name="com.android.bluetooth", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3599, name="sdcard", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3618, name="com.android.systemui", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3721, name="com.google.android.gms.persistent", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3735, name="com.android.phone", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3773, name="wpa_supplicant", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=3975, name="com.google.android.ext.services", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4064, name="com.samsung.android.providers.context", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4106, name="com.google.process.gapps", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4174, name="android.process.media", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4215, name="android.process.acore", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4235, name="com.sec.android.app.launcher", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4343, name="com.google.android.gms", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4418, name="com.sec.android.daemonapp", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4793, name="Settings", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4841, name="com.sec.android.inputmethod", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4866, name="com.sec.bcservice", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4884, name="com.sec.phone", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=4980, name="Contacts", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=5003, name="daemonsu:10149", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=5143, name="com.samsung.android.MtpApplication", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=5173, name="com.android.managedprovisioning", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=5216, name="adbd", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=5967, name="com.samsung.android.beaconmanager", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6102, name="com.samsung.android.sm.devicesecurity", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6184, name="com.samsung.android.scloud", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6483, name="com.sec.android.diagmonagent", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6541, name="SideSync", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6721, name="com.sec.spp.push", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6782, name="com.wssyncmldm", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6822, name="com.android.vending", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6845, name="com.google.android.gms.unstable", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=6961, name="com.policydm", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7034, name="com.samsung.android.SettingsReceiver", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7068, name="Google Play Store", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7087, name="Calendar", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7117, name="com.samsung.android.lool", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7303, name="com.sec.android.provider.badge", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7325, name="sh", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7489, name="su", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7494, name="daemonsu:0", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7497, name="daemonsu:0:7489", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7504, name="sush", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7512, name="com.samsung.klmsagent", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7639, name="com.samsung.android.svcagent", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7660, name="Gmail", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7760, name="com.sec.spp.push:RemoteDlcProcess", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7780, name="com.sec.android.app.sns3", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7826, name="com.sec.android.soagent", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7850, name="Samsung Internet", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7869, name="YouTube", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=7914, name="com.sec.spp.push:RemoteNotiProcess", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8088, name="com.android.printspooler", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8110, name="frida-server-15.1.17-android-arm", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8119, name="daemonsu:0:8110", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8120, name="logcat", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8148, name="Galaxy Apps", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8198, name="com.samsung.android.sm.provider", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8303, name="com.sec.android.app.chromecustomizations", parameters={}) 2023-03-20 02:58:53 AM - root - 19 - DEBUG - Process(pid=8479, name="com.android.providers.partnerbookmarks", parameters={}) 2023-03-20 02:58:53 AM - root - 25 - INFO - Hooks completed -
This is a bit off-topic for this thread which features a cheap pre-rooted Android TV box. You might find this thread helpful especially the bit that finds function names in libwvhidl.so
https://forum.videohelp.com/threads/407196-Dumping-L3-from-Android-10-11-and-12 -
Thank you, I apologize for bothering you again-- I didn't realize there'd be that much of a difference between an Android box and an Android tablet, since every tutorial I've seen talks about a different Android device. All the best. : )
-
hi , does your sumsang tab s2 device have CDM module ? because it looks like have a too old Android version. just install an app called "DRMinfo" from google play and check it if it is L3. i had ever want to dump keys from "redmi note 4x", android 7.0, got some strange problems like yours , and finally when i checked the DRM level ,i found it is none .

-
Thanks so much for your information, man! *checks* Oh! L1, it says! It says "Security Level: L1, Max Number of Sessions: 64, and OEM Crypto API Version: 11"! I didn't even notice the L1 part when I looked last, I probably need to override that to make it use L3 all the time.
EDIT: I was able to get a friend with a 64-bit Linux computer to run through the Android Studio method of getting the keys, and it worked perfectly-- the x86 Google API version of Android Pie DOES have Chrome, unlike any of the compatible ARM versions of Android on M1 Mac Android Studio.Last edited by HomeStarRunnerTron; 21st Mar 2023 at 22:16. Reason: Adding more information about how I solved my problem.
-
Hey,
great tutorial! Worked with the bitmovin-alternative on Windows (https://www.tg4.ie); however, I have a question regarding Android Studio and chrome-behaviour. I created a virtual Pixel 6 with the Pie Android Version x86 (chrome pre-installed)
When I try to just play videos on different drm-protected pages, the stream won't start. Either nothing happens, or the page tries to reload on and on and in the end it's the same: Video is not playing. Do you guys have similar problems or guesses what could be the reason for this? -
-
Try installing the latest chrome apk (from https://www.apkmirror.com/apk/google-inc/chrome/ for instance) in your emulator (adb install path-to-chrome-apk.apk)
I had the same problem with another site and I resolved it that way. -
I have a mobile with widevine L1, how do I get the cmd... I followed the same steps that are used for L3, but I had no luck
-
-
-
Dumper seems not work with android phone version 6.0 right? I tried to find the dynamic functions but seem not see any. Two wv files that I can find are libwvm.so and libwvdrm_L1.so. I don't see any file called 'libwvhidl.so'. Is there anyone success to dump with version 6.0? Please share your experience.
-
Similar Threads
-
widevine decryption help
By birbal1 in forum Video Streaming DownloadingReplies: 2Last Post: 5th Dec 2021, 10:11 -
Help with video download and decryption
By herschel in forum Video Streaming DownloadingReplies: 4Last Post: 26th Jul 2021, 04:31 -
How do I get the decryption key
By Bakekalu in forum Video Streaming DownloadingReplies: 6Last Post: 5th Jul 2021, 01:25 -
Cloudfront video download, decryption?
By Md_95 in forum Newbie / General discussionsReplies: 7Last Post: 5th Apr 2020, 07:53 -
Question about decryption of .m2ts files
By mwalimu in forum Blu-ray RippingReplies: 8Last Post: 23rd Jun 2019, 14:47



 Quote
Quote



