Try StreamFab Downloader and download from Netflix, Amazon, Youtube! Or Try DVDFab and copy Blu-rays! or rip iTunes movies!
Closed Thread
Results 61 to 90 of 227
Thread
-
if the bootloader on your device is unlocked, then it's unlikely l1 keys will be provisioned for that device.
see risks here
https://developer.sony.com/develop/open-devices/get-started/unlock-bootloader#warranty
here
https://www.usenix.org/system/files/conference/woot17/woot17-paper-hay.pdf
and with widevinde being modular even certified gets revoked, see
https://support.google.com/android/thread/109544565/why-cdm-widevine-certificate-degra...e-device?hl=en
but I'm sure you know this already.
-
Ah sure, when you realise he created the topic with the title
I'm sure he knows that too.How To Dump L3 CDM From Android Device's (ONLY Talk About Dumping L3 CDMS)
Honestly, I've never come across someone so demanding of people to give him stuff and yet unwilling to either thank others for their work or to do any actual work himself.
-
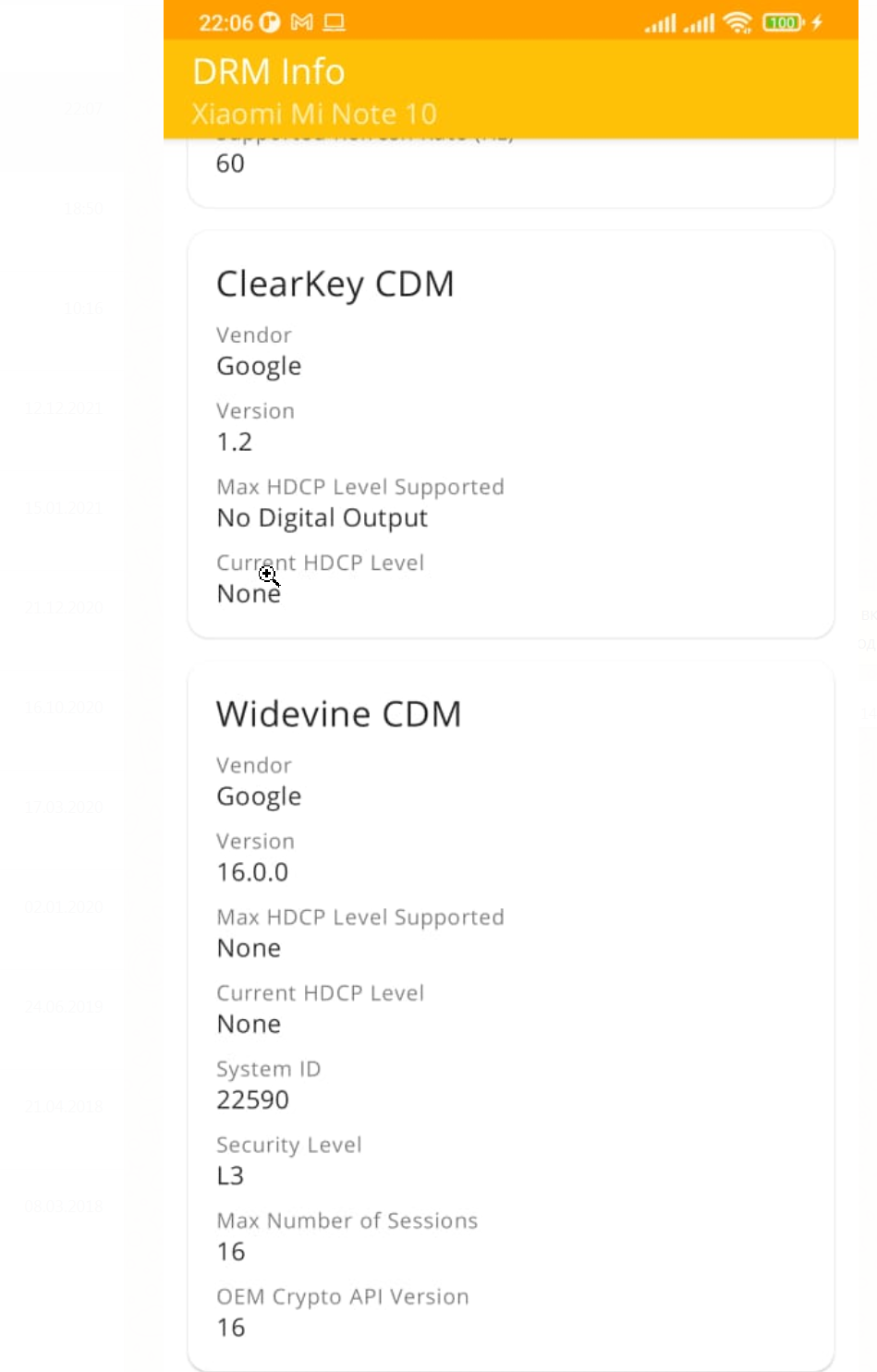
After disabling the liboemcrypto, DRM info is showing L3 ?
If not, you need to access the TWRP recovery menu to do this manually.
After that, if DRM Info shows L3 then restart the script, it should work
The reason is that some device allow the usage of L1 after beeing rooted, but the script only extract L3 so you're not using it, and therefore can't export it
-
i'm trying to have l3 but i can't
i have android 9, root, oemcrypto 13 (in l3), l1 downgraded to l3 by liboem of module's magisk, but only i have the keyboxes -json and bin-, what can i do?
thanks...
edit:
and now, suddenly something fails, but i dont know what. don't found the device, i try reflash the android -root, android 9, l1 downgraded to l3, magisk with module, frida 15.1.14, debbuging- but nothing work. when i write 'adb devices' i see the device.
i tried with py 3.9.6 and 3.9.6
all the requirements are installed. i dont know what to do.
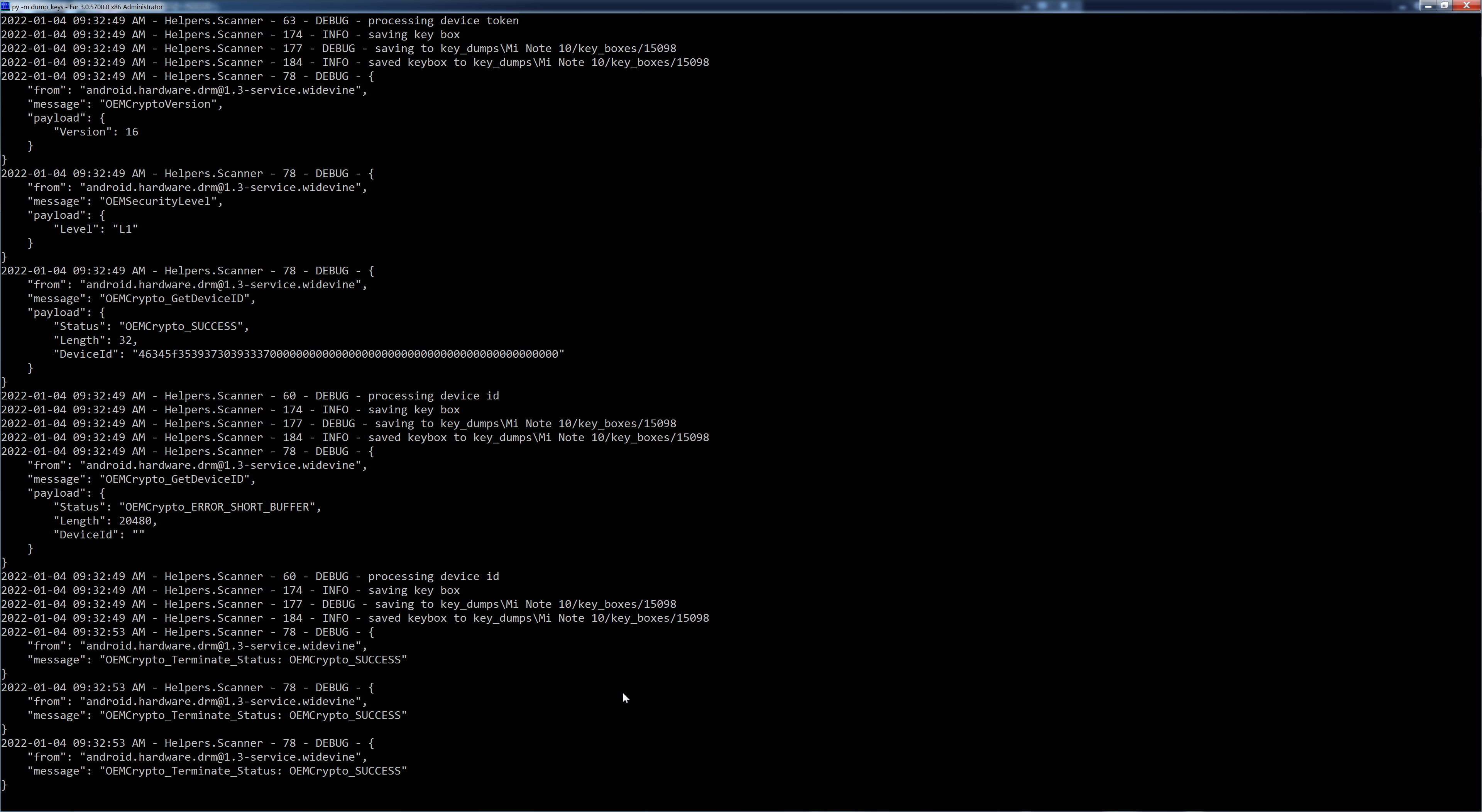
this is the log
D:\py dump_keys.py
Traceback (most recent call last):
File "D:\dump_keys.py", line 14, in <module>
device = frida.get_usb_device()
File "C:\Users\*\AppData\Local\Programs\Python\Python39 \lib\site-packages\frida\__init__.py", line 89, in get_usb_device
return get_device_matching(lambda d: d.type == 'usb', timeout, **kwargs)
File "C:\Users\*\AppData\Local\Programs\Python\Python39 \lib\site-packages\frida\__init__.py", line 97, in get_device_matching
return get_device_manager().get_device_matching(predicate , timeout, **kwargs)
File "C:\Users\*\AppData\Local\Programs\Python\Python39 \lib\site-packages\frida\core.py", line 26, in wrapper
return f(*args, **kwargs)
File "C:\Users\*\AppData\Local\Programs\Python\Python39 \lib\site-packages\frida\core.py", line 58, in get_device_matching
return Device(self._impl.get_device_matching(lambda d: predicate(Device(d)), raw_timeout))
frida.InvalidArgumentError: device not foundLast edited by Jordi22; 6th Jan 2022 at 22:37.
-
Frida is not finding your device. You should not have to reflash the same version that will not fix your problem, if anything the reflashing oldest version your device can take and if available.
Try the following in this order.
1. Restart your device, restart your computer.
2. Make sure USB debugging is enabled on your device, plug to computer. When you're prompted to allow USB debugging, tap on Yes on the device. Is a notification that comes up as soon as you plug in the device.
3. Start the frida server, however you always have done it.
4. Make a backup of the original 'dump_keys.py' script and replace everything inside of it with the following code. Then run it.
5. If this time is successful and you still are only getting the keyboxes, post the log of what happens BEFORE 'All Hooks completed', not after (it may be needed later) nor everything you get. Only what happens before. This will give us an idea of what is up and work from there.Code:#!/usr/bin/env python3 import time import frida import logging from Helpers.Scanner import Scan import sys import threading def get_device(): mgr = frida.get_device_manager() changed = threading.Event() def on_changed(): changed.set() mgr.on('changed', on_changed) device = None while device is None: devices = [dev for dev in mgr.enumerate_devices() if dev.type =='usb'] if len(devices) == 0: print ('Waiting for usb device...') changed.wait() else: device = devices[0] mgr.off('changed', on_changed) return device; logging.basicConfig( format='%(asctime)s - %(name)s - %(lineno)d - %(levelname)s - %(message)s', datefmt='%Y-%m-%d %I:%M:%S %p', level=logging.DEBUG, ) device = get_device() scanner = Scan(device.name) logging.info(f'Connected to {device.name}') logging.info('scanning all processes for the following libraries') for process in device.enumerate_processes(): logging.debug(process) if 'drm' in process.name or 'mediaserver' in process.name: libraries = scanner.find_widevine_process(device, process.name) if libraries: for library in libraries: scanner.hook_to_process(device, process.name, library) logging.info('Hooks completed') while True: time.sleep(1000)
-
hi! works! maybe the dump_keys.py original is the problem?
i run the script but, again, i get keyboxes -json and bin-
i post here the log before 'all hooks completed'
Code:D:\>py dump_keys.py Waiting for usb device... 2022-01-07 06:53:21 AM - root - 38 - INFO - Connected to Redmi Note 7 2022-01-07 06:53:21 AM - root - 39 - INFO - scanning all processes for the following libraries 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=1, name="init", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=594, name="init", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=595, name="init", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=596, name="ueventd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=614, name="mqsasd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=617, name="logd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=618, name="servicemanager", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=619, name="hwservicemanager", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=620, name="vndservicemanager", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=632, name="qseecomd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=635, name="qseecomd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=662, name="android.hardware.gatekeeper@1.0-service-qti", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=663, name="android.hardware.keymaster@4.0-service-qti", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=664, name="vold", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=674, name="magiskd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=769, name="android.hidl.allocator@1.0-service", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=770, name="healthd", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=771, name="android.hardware.audio@2.0-service", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=772, name="android.hardware.bluetooth@1.0-service-qti", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=773, name="android.hardware.camera.provider@2.4-service", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=774, name="android.hardware.cas@1.0-service", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=775, name="android.hardware.configstore@1.1-service", parameters={}) 2022-01-07 06:53:22 AM - root - 41 - DEBUG - Process(pid=776, name="android.hardware.drm@1.0-service", parameters={}) 2022-01-07 06:53:23 AM - Helpers.Scanner - 82 - INFO - Running libwvdrmengine.so at 0x77a44c1000 2022-01-07 06:53:23 AM - root - 41 - DEBUG - Process(pid=777, name="android.hardware.drm@1.1-service.clearkey", parameters={}) 2022-01-07 06:53:24 AM - root - 41 - DEBUG - Process(pid=778, name="android.hardware.drm@1.1-service.widevine", parameters={}) 2022-01-07 06:53:25 AM - Helpers.Scanner - 82 - INFO - Running libwvhidl.so at 0x7969c87000 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=779, name="android.hardware.graphics.allocator@2.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=780, name="android.hardware.graphics.composer@2.1-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=781, name="android.hardware.health@2.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=782, name="android.hardware.ir@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=783, name="android.hardware.light@2.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=784, name="android.hardware.memtrack@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=785, name="android.hardware.power@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=786, name="android.hardware.sensors@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=787, name="android.hardware.thermal@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=788, name="android.hardware.usb@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=789, name="android.hardware.vibrator@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=790, name="android.hardware.wifi@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=791, name="vendor.display.color@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=792, name="vendor.qti.esepowermanager@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=793, name="vendor.qti.gnss@2.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=794, name="vendor.qti.hardware.alarm@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=795, name="vendor.qti.hardware.perf@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=796, name="vendor.qti.hardware.qdutils_disp@1.0-service-qti", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=797, name="vendor.qti.hardware.qteeconnector@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=798, name="vendor.qti.hardware.soter@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=799, name="vendor.qti.hardware.tui_comm@1.0-service-qti", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=800, name="fidoca", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=801, name="vendor.xiaomi.hardware.misys@1.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=802, name="vendor.xiaomi.hardware.misys@2.0-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=803, name="tidad@1.1", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=804, name="vsimd", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=806, name="qrtr-ns", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=808, name="rmt_storage", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=809, name="tftp_server", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=813, name="pm-service", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=814, name="pd-mapper", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=816, name="audioserver", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=817, name="lmkd", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=818, name="surfaceflinger", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=819, name="thermalserviced", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=834, name="sensors.qti", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=911, name="pm-proxy", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=912, name="mm-pp-dpps", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1101, name="cnd", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1103, name="dpmQmiMgr", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1104, name="time_daemon", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1105, name="thermal-engine", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1106, name="adsprpcd", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1107, name="adsprpcd", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1108, name="mlipayd@1.1", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1110, name="fidoca", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1111, name="imsqmidaemon", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1116, name="imsrcsd", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1117, name="hvdcp_opti", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1118, name="smcinvoked", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1119, name="zygote64", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1120, name="zygote", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1121, name="shelld", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1122, name="fdpp", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1132, name="cameraserver", parameters={}) 2022-01-07 06:53:25 AM - root - 41 - DEBUG - Process(pid=1134, name="drmserver", parameters={}) 2022-01-07 06:53:26 AM - Helpers.Scanner - 82 - INFO - Running libmediadrm.so at 0xe8d94000 2022-01-07 06:53:26 AM - root - 41 - DEBUG - Process(pid=1135, name="incidentd", parameters={}) 2022-01-07 06:53:26 AM - root - 41 - DEBUG - Process(pid=1136, name="installd", parameters={}) 2022-01-07 06:53:26 AM - root - 41 - DEBUG - Process(pid=1138, name="keystore", parameters={}) 2022-01-07 06:53:26 AM - root - 41 - DEBUG - Process(pid=1141, name="mediadrmserver", parameters={}) 2022-01-07 06:53:27 AM - Helpers.Scanner - 82 - INFO - Running libmediadrm.so at 0x7504b40000 2022-01-07 06:53:27 AM - root - 41 - DEBUG - Process(pid=1153, name="media.extractor", parameters={}) 2022-01-07 06:53:27 AM - root - 41 - DEBUG - Process(pid=1154, name="media.metrics", parameters={}) 2022-01-07 06:53:27 AM - root - 41 - DEBUG - Process(pid=1155, name="mediaserver", parameters={}) 2022-01-07 06:53:28 AM - Helpers.Scanner - 82 - INFO - Running libmediadrm.so at 0xe8e94000 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1161, name="miuibooster", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1162, name="netd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1164, name="perfservice", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1165, name="statsd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1167, name="storaged", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1169, name="wificond", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1170, name="media.codec", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1171, name="wifidisplayhalservice", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1173, name="cnss-daemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1174, name="ssgqmigd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1175, name="ssgtzd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1176, name="mlid", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1178, name="loc_launcher", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1180, name="ATFWD-daemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1181, name="qdmastatsd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1182, name="seemp_healthd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1183, name="seempd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1187, name="checknv", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1260, name="lowi-server", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1261, name="xtwifi-inet-agent", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1262, name="xtwifi-client", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1263, name="slim_daemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1268, name="gatekeeperd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1272, name="xtra-daemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1283, name="tombstoned", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1293, name="android.hardware.biometrics.fingerprint@2.1-service", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1363, name="seempd_sphinx", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1366, name="seempd_spa", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1373, name="qcrild", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1398, name="imsdatadaemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1401, name="ipacm-diag", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1414, name="msm_irqbalance", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1419, name="ipacm", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1431, name="qcrild", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1434, name="qti", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1442, name="netmgrd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=1444, name="port-bridge", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2350, name="system_server", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2545, name="wpa_supplicant", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2549, name="com.google.android.inputmethod.latin", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2566, name="com.android.systemui", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2591, name="webview_zygote", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2614, name="iptables-restore", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2631, name="ip6tables-restore", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2769, name="Ajustes", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2891, name=".dataservices", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2904, name="com.qualcomm.qti.telephonyservice", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2918, name="se.dirac.acs", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2933, name="com.android.phone", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=2945, name="com.miui.home", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3024, name="com.google.android.ext.services", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3050, name="com.qualcomm.qcrilmsgtunnel", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3248, name="com.google.android.gms.persistent", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3292, name="charge_logger", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3299, name="mcd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3329, name="cnss_diag", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3330, name="tcpdump", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3469, name="com.google.process.gservices", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3485, name="Google", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3516, name="com.goodix.fingerprint", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3549, name="com.miui.daemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3578, name="com.android.se", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3600, name="com.xiaomi.xmsfkeeper", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3647, name="com.tencent.soter.soterserver", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3671, name="com.miui.face", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3792, name="com.android.smspush", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=3887, name="com.google.android.gms", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4077, name="com.lbe.security.miui", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4134, name="com.xiaomi.location.fused", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4331, name="ims_rtp_daemon", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4403, name="com.xiaomi.xmsf", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4464, name="Google Play Store", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4554, name="Seguridad", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4728, name="com.mi.android.globalminusscreen", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=4919, name="com.miui.powerkeeper", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=5107, name="com.facemoji.lite.xiaomi", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=5266, name="com.android.chrome", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=5489, name="com.android.chrome:privileged_process0", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=5585, name="com.miui.analytics", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=6047, name="Chrome", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=6166, name="com.xiaomi.joyose", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=6782, name="FridaServer", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=6870, name="com.android.chrome:sandboxed_process0", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=7061, name="com.android.chrome:sandboxed_process0", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=7188, name="android.process.media", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=7230, name="com.android.settings", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=7501, name="com.google.android.gms.unstable", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=7724, name="com.android.bluetooth", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8100, name="com.miui.micloudsync:sync", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8127, name="com.miui.cloudservice", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8341, name="com.miui.mishare.connectivity", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8382, name="com.xiaomi.account:accountservice", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8568, name="com.miui.notification:remote", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8639, name="com.miui.wmsvc", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8675, name="com.qualcomm.qti.qms.service.connectionsecurity", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8706, name="com.qualcomm.qti.smcinvokepkgmgr", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8725, name="com.qualcomm.qti.smq", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8744, name="com.xiaomi.discover", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8833, name="com.xiaomi.mi_connect_service", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8872, name="com.xiaomi.mipicks:guard", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8887, name="mdnsd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8906, name="GetApps", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8919, name="com.xiaomi.providers.appindex", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=8942, name="Official TWRP App", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9015, name="adbd", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9016, name="com.facemoji.lite.xiaomi:push", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9039, name="com.android.providers.calendar", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9087, name="com.miui.android.fashiongallery", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9155, name="Cámara", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9241, name="com.google.android.googlequicksearchbox:search", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9329, name="com.google.process.gapps", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9375, name="frida-server-15.1.14-android-arm64", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9379, name="logcat", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9391, name="Magisk", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9429, name="frida-helper-32", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9465, name="com.xiaomi.simactivate.service", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9490, name="com.xiaomi.finddevice", parameters={}) 2022-01-07 06:53:28 AM - root - 41 - DEBUG - Process(pid=9515, name="com.google.android.apps.wellbeing", parameters={}) 2022-01-07 06:53:28 AM - root - 47 - INFO - Hooks completed
-
when DRM Info must show L3 ? In my case it shows L1 - and it works like a charm.
The only importent is, to start a playback before start the script.
1. Start playback and stop
2. Start the dumper
3. Play again
If i start dumper before playback soething, i get this:
py dump_keys.py
2022-01-06 11:07:45 AM - root - 16 - INFO - Connected to Sony
2022-01-06 11:07:45 AM - root - 17 - INFO - scanning all processes for the following libraries
2022-01-06 11:07:45 AM - root - 19 - DEBUG - Process(pid=1, name="init", parameters={})
... (delete some lines)
2022-01-06 11:07:50 AM - root - 25 - INFO - Hooks completed
nothing happend more !
If i playback first something and start dumper then, i get
py dump_keys.py
2022-01-06 11:29:08 AM - root - 16 - INFO - Connected to Sony
2022-01-06 11:29:08 AM - root - 17 - INFO - scanning all processes for the following libraries
2022-01-06 11:29:08 AM - root - 19 - DEBUG - Process(pid=1, name="init", parameters={})
... (delete some lines)
2022-01-06 11:29:13 AM - Helpers.Scanner - 75 - DEBUG - {
"from": "Dynamic Function",
"message": "L3 RSA Key export function found: ulns"
}
2022-01-06 11:29:13 AM - Helpers.Scanner - 82 - INFO - Running libmediadrm.so at 0xac2be000
... (delete some lines)
2022-01-06 11:29:13 AM - root - 25 - INFO - Hooks completed
then i get in the log this entry with export function. Then it works.
-
Is not finding the private key fuction at all. Normally the script indicate when it does. I will take a look and see if I can find it tomorrow and shows you how to update it. In the meantime keep trying different apps that use widevine, as indicated above , pause and run the script while the content is paused.
Until you see something like this on your logs, it not going to get you the PK.
sometimes is not named the same or not available in the script.Code:from": "Dynamic Function", "message": "L3 RSA Key export function found: whatever name"
-
You will want to remove that entire log, it has your device ID. But you are getting the same results as the other user. Its not intercepting the private key fuction and not hooking it. Although your case appear to be a very recent build of it and may not be very successful on it depending how much it has changed. If any of you can PM me libwvhidl.so, libmediadrm.so, libwvdrmengine.so from your device I may be able to help. I was unable to find one online and even if I do, it may not apply to your devices. You would need a root explorer app to be able to navigate into the system files and copy those shared libraries.
-
Disassembly may not be required....
What I did for this was to modify the dumper JS to log out the names of all exports that it didn't hook. It was pretty obvious (in Android 10 at least) which one was the dynamic function I needed based on the short, random character name. Worked like a charm.
-
hi

I'm looking for an answer.
I have:
SM-G930F - Samsung Galaxy S7
android 8
frida-server-15.1.14-android-arm
Such errors after firing the dumper:
PS C:\Users\USER\Desktop\L3\dumper-main\dumper-main> py dump_keys.py
2022-01-10 08:18:43 PM - root - 16 - INFO - Connected to SM G930F
2022-01-10 08:18:43 PM - root - 17 - INFO - scanning all processes for the following libraries
Traceback (most recent call last):
File "C:\Users\USER\Desktop\L3\dumper-main\dumper-main\dump_keys.py", line 18, in <module>
for process in device.enumerate_processes():
File "C:\Users\USER\AppData\Local\Programs\Python\Pytho n39\lib\site-packages\frida\core.py", line 26, in wrapper
return f(*args, **kwargs)
File "C:\Users\USER\AppData\Local\Programs\Python\Pytho n39\lib\site-packages\frida\core.py", line 110, in enumerate_processes
return self._impl.enumerate_processes(*args, **kwargs)
frida.NotSupportedError: unable to handle 64-bit processes due to build configuration
PS C:\Users\USER\Desktop\L3\dumper-main\dumper-main>
Similar Threads
-
How to use working CDM to decrypt L1 content
By mathieuthibault in forum Video Streaming DownloadingReplies: 15Last Post: 21st Oct 2023, 07:41 -
Widevine CDM
By KyoGo in forum Video Streaming DownloadingReplies: 8Last Post: 19th Jul 2023, 03:43 -
new cdm
By ThunderRanger in forum Video Streaming DownloadingReplies: 0Last Post: 6th May 2020, 03:16 -
Android Players vs LavFilters-MadVR? Looking to go to Android BOX
By therock003 in forum Software PlayingReplies: 3Last Post: 20th Jul 2018, 11:11 -
Android:i want to play this channel in vlc android application (vlc.apk)
By sam jack in forum Newbie / General discussionsReplies: 5Last Post: 16th Oct 2017, 16:10