I finally took the time to switch my wifi router to WPA encryption. I was using WEP before. I decided since my other devices supported WPA I might as well do it.
Now that I have done it I wonder - is WPA really better than WEP? Was I more vulnerable to attack under WEP than WPA?
I had checked and my Nintendo WII supported WPA and my older wifi card on my XP desktop supports WPA so I decided to switch. My xbox 360 and ps3 are hardwired to my router so those weren't affected.
eDIT - Out of curiosity my zune 30gb model with the latest zune update does support wpa. It was previously set up to do wireless (synch with pc and limited marketplace functionality - not the full internet like the new zune hd does however). I was able to turn on the wireless broadcast on the zune and then it found my network and I plugged in my password and I was good to go.
Try StreamFab Downloader and download from Netflix, Amazon, Youtube! Or Try DVDFab and copy Blu-rays!
+ Reply to Thread
Results 1 to 30 of 35
Thread
-
Donatello - The Shredder? Michelangelo - Maybe all that hardware is for making coleslaw?
-
There are freely downloadable apps for both OSX and Windows that utilize the wireless connections in your notebook to detect WEP-encrypted WiFi networks and then crack them in about 3 minutes.
So, yes, WPA is much more secure; and, yes, you were quite vulnerable using WEP. HOWEVER, be sure you use a long password (23 characters should be sufficient).
Read this: http://news.cnet.com/8301-13554_3-9822842-33.html -
The level of security you need really depends on where you are located. Routers only transmit a short distance, usually less than a 1/4 mile. Or more commonly, even less, depending on the antenna configuration, location, the output power, and sometimes depending on the receiving antenna. I've played with a parabolic dish and was able to double my WiFi reception range.
Check the wireless signals around you and see what's out there at your location. If you only see a few, lower security threat.
I've used WirelessMon to check out the signals in my neighborhood. It has a 30 day trial. http://www.passmark.com/products/wirelessmonitor.htm
If you're next to a urban internet café with lots of web savvy teenagers, the more protection, the better. If you're in the 'burbs', protection still needed, but you aren't as likely to be attacked.
If you're in the 'burbs', protection still needed, but you aren't as likely to be attacked.
But I agree, WPA is much better than WEP. I use WPA2-PSK [AES] for my laptop. If you want a bit more security, disable your SSID Broadcast and you're likely not to be found at all. And use a higher level password for your encryption PW and also use a better PW for your router. It's funny how many routers don't use any encryption and if they do, the password to access the router is 'password'.
If you are worried about financial transactions being compromised over a wireless connection, they almost always use https, which already has a strong layer of security. -
Be sure to use WPA2:
http://www.electronista.com/articles/09/08/27/wpa.1.minute.hack/
Japanese researchers today revealed that they have developed a crack that can break WPA (Wireless Protected Access) encryption on a Wi-Fi network within a minute. -
Thanks for the info.
Fyi I apparently can't use wpa2 on my wifi card on my desktop. It's an older netgear G wifi card and does support wpa but not wpa2 by the looks of it.
Also its weird I had trouble logging on this morning. It was fighting between windows control of the adapter and the netgear configuration utility. It took awhile but I got back on.Donatello - The Shredder? Michelangelo - Maybe all that hardware is for making coleslaw? -
Commonly believed, but bad idea.Originally Posted by redwudz
Originally Posted by George Ou -
You either use "Windows Zero Configuration" or a third-party app (usually bundled with the hardware).Originally Posted by yoda313
If the latter, you need to deactivate WZC, they both can't work simultaneously. Usually this is done by the new app, but maybe you reactivated WZC by mistake.
See http://www.ezlan.net/wzc.html -
There are also some instances where WPA2 on Snow Leopard isn't reliable periodically dropping the connection. I can confirm this. I switched the router to WPA only (from WPA/WPA2) and this resolved the issue 100%. I suspect it may not apply to all wireless access points but mine are the 2Wire AT&T DSL gateway and a Netgear MIMO WPN824; Apple's AirPort Extreme has also been reported as having this problem (but I don't own this one so I can't confirm).
-
I had a lot of problems recently with my Netgear router dropping the signal to my laptop. The router wouldn't show at all on the laptop. My netbook also had problems with WPA2 and losing the signal. A router update seemed to have fixed both problems.
I also have my router set up for fixed addresses. I find that much more reliable than DHCP. (Dynamic Host Configuration Protocol) I don't normally turn off SSID, but it does keep the router from showing up on other's computers. Unless you have sophisticated hackers around, it's not likely they will try to break into your system if they don't see it listed on their machines. But I agree turning off SSID will give you occasional problems as the computers may not always find the router quickly.
I live in the suburbs and there isn't anyone nearby with enough computer experience to be much of a threat for a attack. And I do use firewalls that keep out most intrusions if they were to get into the router. Checking your router logs on occasion may alert you to something odd going on. You can also set up your router to just recognize your computers and to ignore all others easily by using MAC address filtering. If you host guests occasional on your system, then that may be a problem.
If you don't have WPA2, at least use a strong password and a decent firewall. And change the name of your router. When it IDs as a Linksys or a D-link, not hard to guess what the address range is. And if it uses 'admin' as the login, you just need to guess the password.
And change the name of your router. When it IDs as a Linksys or a D-link, not hard to guess what the address range is. And if it uses 'admin' as the login, you just need to guess the password.
-
Yeah turning it off causes problems with my Linksys router but on my old D-Link it wouldn't cause problems. Having at least 13 characters for a network key is a good idea and changing it every few months is also.Originally Posted by AlanHK
Also make sure you enable stealth mode on your firewall, Linksys calls it "Block Anonymous Internet Requests".
Vista and 7 are more secure than XP when using a unsecured network(internet cafe) but here's a few tips for you XP users:
1.Make sure you have SP3!
2.Turn off Remote Assistant.
3.Turn off file and printer sharing.
4.Use a better firewall. -
Originally Posted by AlanHK
Hey there,
Well I got around it. I deleted the netgear connection utility from the startup menu so now Windows does the connection. It connected automatically on its own without any hassle.
Thanks for the info though.Donatello - The Shredder? Michelangelo - Maybe all that hardware is for making coleslaw? -
The worst place to run wireless routers for security would be a dense apartment complex in Silicon Valley. First, they all know how to hack to your hard drives, second the only way to find an open WiFi channel is to hack somebody else.
All this would also apply to high tech customer hotels anywhere in the world.Recommends: Kiva.org - Loans that change lives.
http://www.kiva.org/about -
Yes, but in that case you would expect everyone to be at the same level of play. It should not be pro vs high school. The defense would not only be ready for the play but also trying to stuff the offense in the backfield...or in tech terms: running a honeypot to turn the hunter into the hunted...but no one would ever do that 8)Originally Posted by edDV
-
In the burbs, you need to worry about the teens close by.
Actually within a mile or so if they use a yagi. In the hills it could be a couple dozen miles.
 Recommends: Kiva.org - Loans that change lives.
Recommends: Kiva.org - Loans that change lives.
http://www.kiva.org/about -
Most of what anyone can do, if they do manage to connect to your router, is gain access to your internet connection and use your bandwidth. If they where to start downloading large files they could kill your monthly cap or use it for illegal activities and make it look like it came from your connection. Access to other connected computers would depend upon firewall and file sharing permissions.Originally Posted by edDV
I might have missed it, but the one thing I have not seen mentioned here is ensuring that remote management of the router is disabled.
It always amazes me as to how many people do not enable any security at all. Possibly because they just do not have the knowledge of what can happen if they don't or else their internet connection does not work if they enable it, so they disable it...when I check available networks in my area there are about 50. Most are WAP 1/2, a few WEP and 4 or 5 are no security with default router names. Who would start hacking the WAPs or the WEPs when there are some wide open? Scary...and probably the same in just about every high density metropolitan residential area. -
Yes, around my area there are several wide open. I figure WPA2-PSK makes you less a target. I also shield the wireless router from the down hill side and turn down signal strength. The opposing ridge has no cable or DSL service. I figure some are DX'ing for a wireless connect.
Recommends: Kiva.org - Loans that change lives.
http://www.kiva.org/about -
Do you know what netgear calls their version of that so I can disable mine?Originally Posted by video_head
Also where would you change your network name on the router? Should it be something inconspicuous or can any name do as long as its not the default? Obviously I wouldn't be stupid enough to use my real name or anything - even though our neighbors obviously know us but its the potential "prowlers" I'd be thinking of.
Thanks for all the advice and suggestions. I'm glad now I did switch to wpa.
Edit - oh also would that prevent me from making changes on my own router from my other computer wirelessly? Would I only be able to access the router with the computer that is hardwired to it?Donatello - The Shredder? Michelangelo - Maybe all that hardware is for making coleslaw? -
Remote management is usually in admin and is disabled by default, it allows you to access the settings on a specified port. The network name is usually in wireless security and it's the name being broadcasted, use your initials or an alias such as YODA. I can't believe some of my neighbors use their full names.
-
an extra layer of protection i use is to turn off broadcasting. no one can find the wireless connection at all without knowing the workgroup name.
-
Nope. It's just the SSID name that's being broadcast. When you change it, it should show up as the new name on all your PCs. And I would be careful making changes on your router over a wireless connection. You could drop the signal and corrupt something in the router, though that's unlikely. Definitely don't update your router's firmware over a wireless connection.Originally Posted by yoda313

If you use a decent level of encryption with your router, a secure password, add MAC filtering, and use fixed addresses for your computers, you would be fairly safe just about anywhere.
As mentioned, someone piggybacking through your router to your ISP is probably the most common danger, not them hacking into your PCs.
Here's what my local area looks like at present. The Meridian names are the ISP's WiFi transceivers:
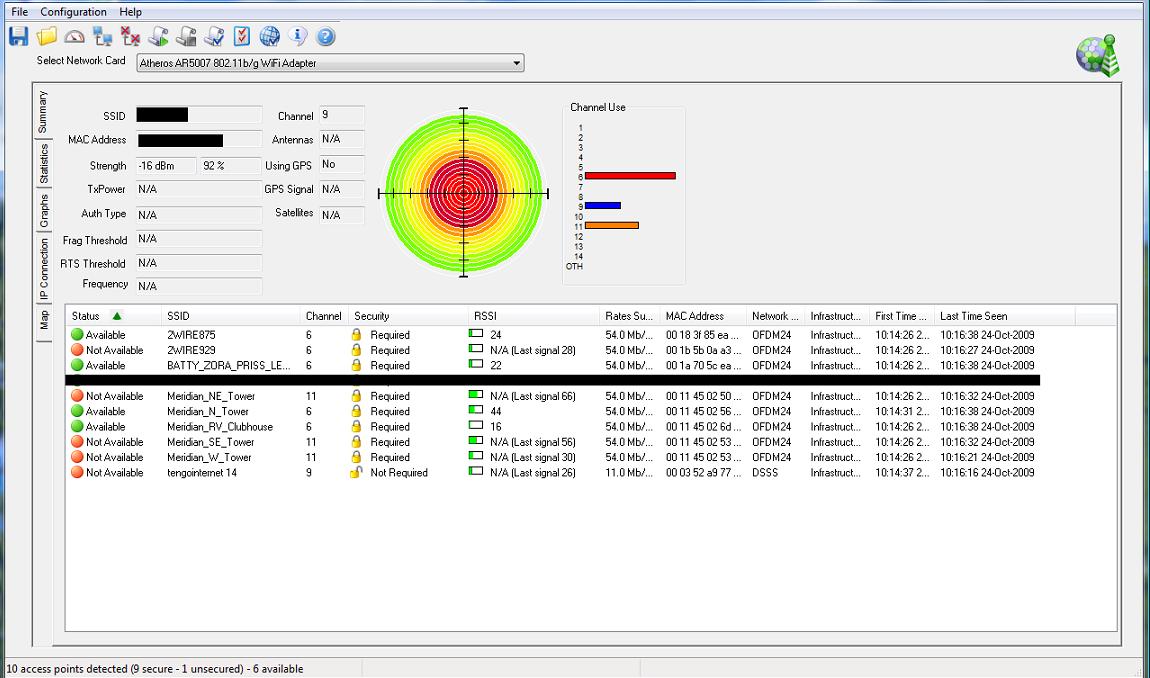
-
It should just be called remote management. I have never seen a manufacturer use a pet name for it.Originally Posted by yoda313
The network name (or router name) is in the management settings on the administration page. It is usually a web page at the routers IP address. You then log in with user name and password. You can use any network name you wish. In my area they are people's names, business names, plugs for sport teams (seems to be a war going on there) and one is even called "Macs Rule". On that point, I disagree with a name that draws attention to yourself. The quiet mouse gets the cheese, the loud mouse gets eaten by the cat. Using a name like "My Unhackable Network" would just draw every script kiddie and true hacker to try harder than casual. You will get "drive by" attempts. They are usually just looking for easy prey. Using good security practices will usually make them move on to an easier target.
Any computer connected to the router can access the administration page. Just browse to the router's IP address, enter the username and password and you have full access to the management settings - see why it is so important to change the default? To be connected to the router though the device needs the network key. This should never be a problem because your network key is long and strong, right?
Another little security trick I like to use is changing the router's default IP address. Change the last number to something other than the default between 0 and 255. Just remember what you changed it to, because you have to hard reset the router to get back the defaults. Anyone trying to hack your router would probably get frustrated when they can not find the administration page and just move on. Remote management allows access to the administration page from the WAN side so it is important that this be dissabled unless you specifically need it.
Good router security practices:
- Change the administration login name and password.
- Use the strongest security scheme that your connected devices support: WPA2, WPA, WEP.
- Use a long and strong key: at least 25 characters with upper and lower case letters and numbers. Do not use words found in the dictionary.
- Physically ensure that remote management is dissabled - do not trust that it was dissabled at the factory.
- Change the default IP address of the router.
- Set the maximum number of DHCP assignable addresses to the maximum number of devices you will connect or use fixed IP numbers or only allow assigned MAC addresses to connect if possible (MAC addresses can be spoofed so it is still not fool proof).
- Enable connection logs.
- Audit your security occassionally: check who is connected to your network, check that remote management has not been enabled, check logs, check that your security scheme has not been changed. Do this frequently after making changes, if no problems you can lower the vigilance.
I hope this helps. -
Wrong.Originally Posted by minidv2dvd
A tool like Kismet can listen to the network traffic and when something connects to your "hidden" AP, it grabs the details.http://blogs.zdnet.com/Ou/index.php?p=43&tag=col1;post-454
SSID hiding: There is no such thing as "SSID hiding". You're only hiding SSID beaconing on the Access Point. There are 4 other mechanisms that also broadcast the SSID over the 2.4 or 5 GHz spectrum. The 4 mechanisms are; probe requests, probe responses, association requests, and re-association requests. Essentially, you're talking about hiding 1 of 5 SSID broadcast mechanisms. Nothing is hidden and all you've achieved is cause problems for Wi-Fi roaming -
A simple IP scan will find it in a few seconds.Originally Posted by Video Head
Eg, this freeware: "Advanced IP Scanner".
Useful when I bought an old router with no documentation and had find its admin page, and other network devices. -
hehe - don't know what you're using but nothing has found my wifi ssid with broadcast disabled. it shows up on no wireless device brought here.
-
Try KismetOriginally Posted by minidv2dvd
Don't you think that if making your network "unhackable" was so simple, that everyone would do it? That it would be the default? Why bother with encryption if you can just "turn off the beacon and be invisible"?Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and can sniff 802.11b, 802.11a, and 802.11g traffic.
Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and given time, decloaking) hidden networks, and infering the presence of nonbeaconing networks via data traffic.
It's just a way of making your network break standards, so devices looking for well-behaved networks will indeed not connect. But hacking tools are not so naive. -
you don't seem to understand. since it's not a named network, it isn't findable using normal methods. it would take a determined hacker hours to find it. my son's college computer science major buddies can't log on half the time even if i give them the ssid. i don't care if it's non-standard, it works for me and all my wifi equipment. that's the point.
-
You didn't try Kismet, did you?Originally Posted by minidv2dvd
Here's a tutorial to get you started: http://www.wi-fiplanet.com/tutorials/article.php/3595531
It would take a "determined hacker" two minutes.
You gain nothing over simply using a strong WPA password.
You can hide from people who aren't a threat anyway -- as you say, all you've done is make it hard for legitimate users to log on. -
I agree. It is nothing but another deterent.Originally Posted by AlanHK
Living in Hong Kong you must understand the security issues with automobiles. Every time you park your car in Hong Kong you must worry if it will be safe...how do you protect your automobile in Hong Kong?
Is locking your doors enough? Do you have passive ignition security? Do you use a steering wheel lock? Do you have an alarm? Do you park it on the street or do you have a secure spot? If you have a secure spot, are there security guards? Do they have dogs? Do they have guns? Are they willing to shoot someone dead to protect your automobile?
Security is nothing...if someone is motivated enough to get it, they will... -
If you knew anything about Hong Kong, you'd know that very few people have cars. A bit like Manhattan in that respect. I don't know anyone who does, personally. And security guards here (except in banks) do not have guns. Very few criminals do either, despite what you see in HK movies.Originally Posted by Video Head
But that's another, off-topic, story. Sorry to spoil your analogy -- the good old Slashdot-style car analogy for every occasion. -
I know that very few people in Hong Kong have cars...that is why I used the analogy :POriginally Posted by AlanHK
One of my friends there works with a woman who "drives to work". The distance she walks between the parking lots is greater than the distance between her closet size apartment and her office. But she drives to work and, as I understand it, is of great status importance.
You seemed to completely miss the point...
Similar Threads
-
AACS Bluray encryption
By BIFFtheSTIFF in forum MacReplies: 0Last Post: 17th Jun 2011, 21:26 -
Does GI Joe: Rise of the Cobra use a new encryption...
By rayden54 in forum Newbie / General discussionsReplies: 6Last Post: 2nd Apr 2010, 10:45 -
Best encryption algorithm?
By alegator in forum ComputerReplies: 5Last Post: 10th May 2009, 23:37 -
BD+ encryption blue-ray
By herbapou in forum Blu-ray RippingReplies: 4Last Post: 24th Mar 2009, 07:58 -
how to use WPA wireless protection?
By Rudyard in forum ComputerReplies: 7Last Post: 5th Mar 2009, 16:19




 Quote
Quote